Weekly Significant Activity Report - November 1, 2025
This week’s analysis highlights some of the most significant geopolitical developments involving America’s adversaries—China, Russia, Iran, and North Korea—between October 25 - November 1, 2025.
Summary:
Russia continued advancing on two key Ukrainian strongholds, Pokrovsk and Kupyansk. Its overall progress on both fronts remains incremental and costly.
Russia announced the successful test of two nuclear-powered, nuclear weapons, the Burevestnik cruise missile and the Poseidon torpedo.
Chinese President Xi Jinping and US President Donald Trump met in Busan, South Korea. The leaders agreed to suspend recently imposed trade restrictions but stopped short of announcing a long-term deal to resolve key US-China economic issues.
China took steps to impose its vision of maritime order through newly announced maritime laws and assertive moves in the Yellow Sea.
The People’s Bank of China announced that it had made progress curbing local debt and reducing the number of risky local government financing vehicles.
State-affiliated hackers from China, Russia, and Iran were implicated in new high profile hacks.
North Korea announced its willingness to play a bigger role in Eurasian Security at the Third Minsk International Conference on Eurasian Security in Belarus.
The North Korean navy tested new ship-launched missiles, the second major missile test in two weeks after months of quiet.
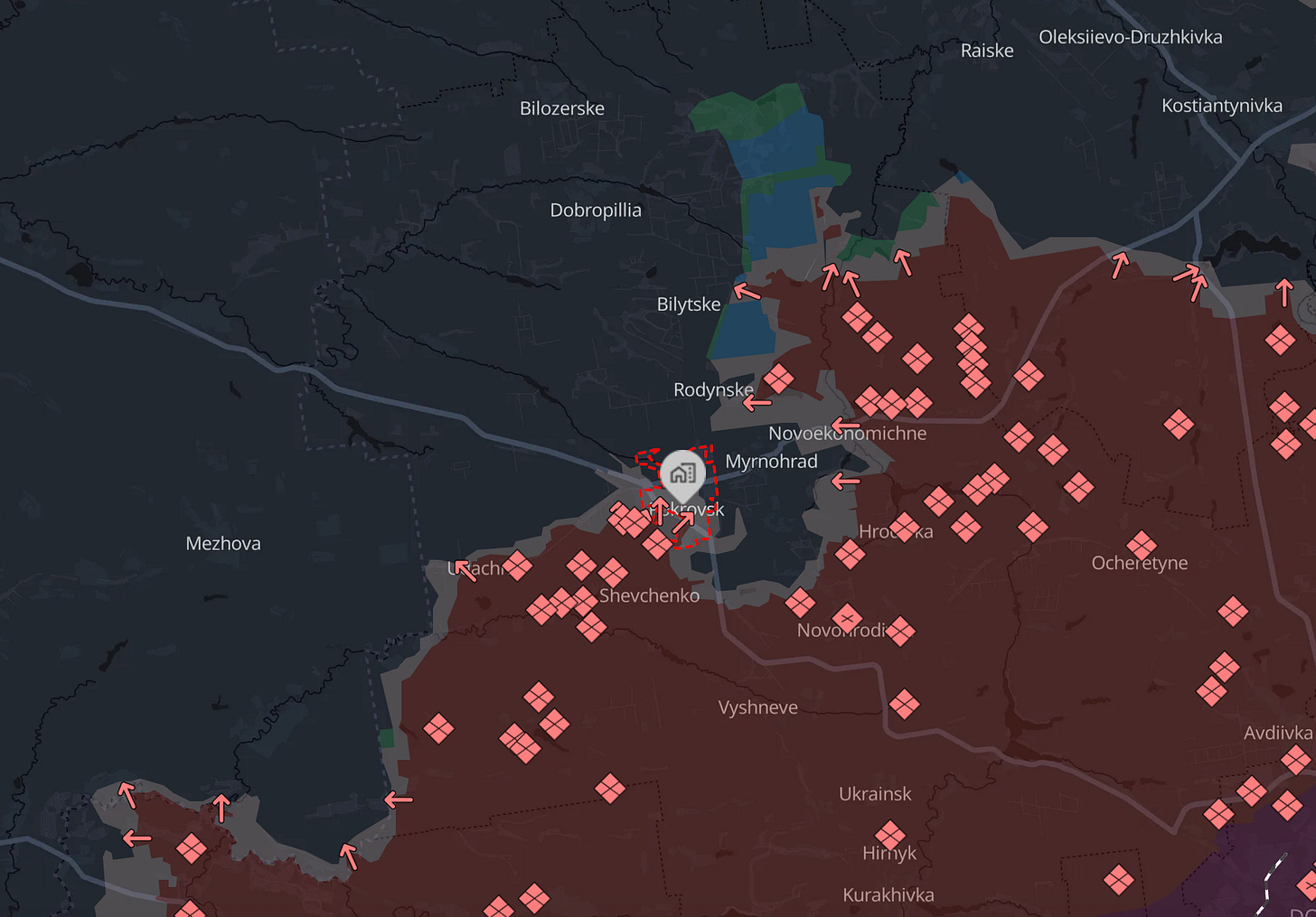
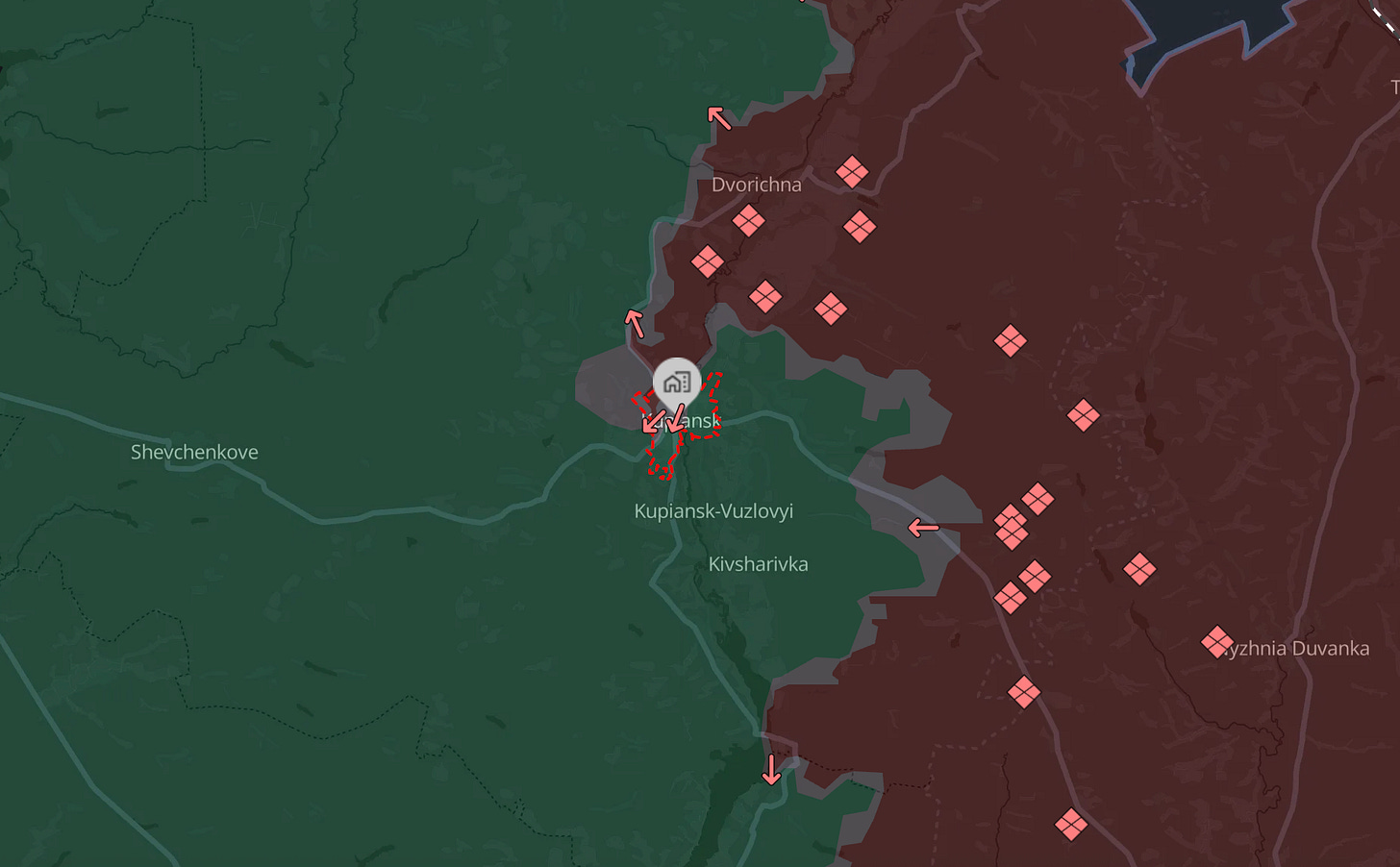
1. RUSSIA CLOSES IN ON POKROVSK AND KUPYANSK
This week the Russian military claimed that it had fully encircled the city of Pokrovsk in Ukraine’s Donetsk oblast and the city of Kupyansk in Kharkiv oblast. The Kremlin offered to conduct a brief truce to allow the media to enter both cities to verify that they were encircled. The announcement followed reports that company-sized elements of Russian soldiers had begun assaulting the city center of Pokrovsk.
Ukraine has denied Russia’s claims to have encircled the cities. However, on October 31, Ukrainian President Volodymyr Zelensky acknowledged that Pokrovsk was under relentless assault by a force of 170,000 Russian troops, and that Russian troops had entered the city.
“The situation in Pokrovsk is difficult. All their forces are there. You know that 170 thousand of the enemy are concentrated in this direction. There are a lot of them. This morning I spoke with the commander-in-chief - there are no changes in Pokrovsk. There are “Russians” in Pokrovsk. Ours are destroying them, destroying them little by little - because we also need to protect the personnel.”
Takeaways:
Russia is clearly advancing on both cities but it has overstated its progress as of right now. According to analysis by the Institute for the Study of War, verified by independent mapping by DeepState, neither city is currently encircled.
Some Russian military bloggers have also voiced their skepticism about the Kremlin’s claims. One prominent Russian milblogger Roman Light suggested that President Vladimir Putin and Chief of the Russian General Staff Valery Gerasimov were deliberately distorting the word “encirclement” because they had told the US that the Russian military was advancing and would achieve certain offensive objectives by the fall if Ukraine did not agree to peace on its terms.
The ongoing siege of Kupyansk represents Russia’s first major attempt to recapture a city it lost during Ukraine’s 2022 counteroffensive. Its capture is unrelated to Russia’s main offensive operations in Donetsk and is likely an effort to take pressure off Russian forces in Pokrovsk. However, the larger objective is probably to achieve a symbolic victory demonstrating that Russia will reclaim all previously ceded Ukrainian territory. The Kremlin will leverage any victory, no matter how costly, to project an image of inevitable triumph and pressure Ukraine and its partners to negotiate an end to the war on Russia’s current terms before they become more expansive.
A breakthrough is unlikely to follow even if Russia is able to seize the two cities in the coming weeks. The victories the Russian military achieved in similar offensive operations in Avdiivka, Bakhmut, and Chasiv Yar depleted its capacity to effectively press its advantage and perform follow-on offensives.
2. RUSSIA COMPLETES NEW WONDER WEAPON TESTS
This week Russia announced that it had successfully completed new tests for its experimental, nuclear-powered, nuclear-armed Burevestnik cruise missile and Poseidon torpedo.
Takeaways:
This topic is covered in depth in this week’s special situation report:
3. XI AND TRUMP MEET AND DECLARE TRADE TRUCE, BUT FINAL DEAL STILL ELUSIVE

On October 30 US President Trump and Chinese President Xi Jinping met in Busan, South Korea following the APEC CEO Summit. The two leaders discussed a variety of issues and agreed to a number of steps to deescalate economic tensions between the two countries. These steps include the following measures:
Chinese Commitments:
Reciprocate tariff reductions with US and suspend port fees for US ships
Export controls on rare earth metals enacted on October 9, 2025 suspended for one year
Purchase a minimum 25M metric tons of soybeans from US farmers over next three years
Port fees for US ships suspended for one year
US Commitments:
“Fentanyl tariffs” on Chinese goods reduced from 20% to 10%
24% reciprocal tariff on Chinese goods suspended for one year
Export restrictions on sales of advanced US technology products to affiliates of Chinese companies suspended for one year
Port fees for Chinese ships suspended for one year
Takeaways:
The agreements struck this week appear to just roll back several recent escalatory moves in the trade war but do not resolve the fundamental issues driving conflict between the US and China. China seeks reduced restrictions on access to advanced technology, for which the US has acted as a gatekeeper. The US aims to mitigate national security risks posed by China’s dominance over critical segments of the global supply chain. These core concerns remain unresolved under the current deal.
Further evidence that fundamental issues remain unresolved can be found in China’s apparent slow rolling of the sale of TikTok to a consortium of US investors. While US Treasury Secretary Scott Bessent has announced that China has provided final approval for a sale, Bessent admitted that negotiations could still continue for months. “In Kuala Lumpur, we finalised the TikTok agreement in terms of getting Chinese approval, and I would expect that would go forward in the coming weeks and months, and we’ll finally see a resolution to that,” Bessent said.
4. CHINA MAKES NEW MOVES TO ASSERT ITS INTERPRETATION OF MARITIME LAW
China Pushing New Maritime Laws
This week China’s National People’s Congress Standing Committee passed a newly revised national maritime law that will take effect on May 1, 2026. According to Chinese state media outlet Xinhua:
“The revised law was approved at the 18th session of the 14th National People’s Congress Standing Committee. Spanning 16 chapters and featuring 310 articles, it adapts to the latest trends in shipping and trade, draws on the latest international maritime conventions, and balances the interests of relevant parties.
“It holds significance for promoting high-quality development in shipping and trade, enhancing marine environmental protection, advancing high-level opening up, and building China into both a maritime power and a shipping power.”
New Report Documents Maritime Confrontation between China and South Korea
According to a new report by the Center for Strategic and International Studies, on September 24 the coast guards of China and South Korea engaged in a 15-hour standoff in the Yellow Sea. The dispute was sparked by the entry of a South Korean research vessel into shared Korean-Chinese waters of the Yellow Sea, known as the Provisional Measures Zone (PMZ).
Takeaways:
China is looking to reshape international maritime law by settling more maritime cases in its courts. The new laws passed this week are part of an effort to encourage more third parties to apply Chinese interpretations of maritime law to their operations. By building a substantial body of legal precedent in maritime disputes, China can advance its expansive maritime interests. These interests stretch from the South China Sea, to the broader Indian and Pacific Oceans and increasingly to the Polar regions as well.
The September standoff exemplifies increasingly assertive behavior by Chinese maritime forces in the Yellow Sea. China’s presence in the Yellow Sea in recent months has come to resemble its aggressive moves in the South China Sea over the last decade.
In early 2025 China began constructing large steel structures in the PMZ in apparent violation of a 2001 agreement with South Korea to jointly govern and share the waters. China calls the structures aquaculture facilities, but their large size and overall design suggest dual use as military facilities. One of the structures, a mobile rig known as Atlantic Amsterdam, has a helipad and can house between 60-136 people.

Atlantic Amsterdam pictured in the Yellow Sea Source: Maritime Executive Since the structures appeared China has attempted to impose unilateral restrictions of South Korean navigation in the region due to military exercises, another violation of the 2001 PMZ agreement.
China may replicate its strategy for controlling the South China Sea in the Yellow Sea, expanding its footprint further east in the PMZ. If the same playbook is followed China would construct additional dual-use infrastructure to serve as military outposts and deploy fleets of civilian vessels coordinated by the China Coast Guard to harass South Korean ships. China would then reject Seoul’s attempts to resolve the dispute through the UN Convention on the Law of the Sea, instead insisting the matter be adjudicated in Chinese courts under its newly established maritime law.
5. CHINA CLAIMS TO HAVE REDUCED RISKY LOCAL GOVERNMENT DEBT
This week People’s Bank of China Governor Pan Gongsheng told China’s National People’s Standing Committee that since early 2023 the country had reduced the total number of local government financing vehicles (LGFVs) by 71% and cut their corporate debt burden by 62%.
Takeaways:
The reduction in the number of LGFVs is an important step for the CCP to get local government debt under control. LGFVs are a type of private-public partnership bond that is not officially held on the local government’s balance sheet. LGFVs have become the largest means of funding for many local government infrastructure projects since 2008.
The International Monetary Fund’s 2024 Financial System Stability Assessment for China estimates the total outstanding liabilities for LGFVs to amount to 47% of GDP as of the end of 2023.
The People’s Bank of China has been reducing the number of LGFVs through a 10T yuan ($1.4T) debt substitution program. In this program the Central government issues special purpose bonds which swap out the off-balance-sheet debt with debt registered to the local government. This helps ease some of the debt burden and makes officials more accountable to their actual financial performance.
Fitch Ratings has judged this debt substitution program to be a good start for addressing growing local government debt, but one which has mostly been directed toward smaller regions. This has helped support areas with the least resources but left larger provinces—where much more debt is located—vulnerable. Fitch also notes that the debt substitution program does not reduce overall public sector debt in China, it just redistributes it. It may however help control its growth by reducing interest rates for local borrowers.
6. NEW HIGH PROFILE HACKS BY CHINA, RUSSIA, AND IRAN
Chinese Hackers Target European Diplomats
On October 30, cyber security firm Arctic Wolf Labs reported that it had identified with high confidence that hackers from Chinese Advanced Persistent Threat (APT) Group UNC6384, had conducted a cyber espionage campaign targeting European officials with complex spear-phishing attacks between September and October 2025. Arctic Wolf researchers identified evidence that Belgian and Hungarian diplomats had been targeted as well as government officials from Serbia.
Russian Hackers Target Ukrainian Insurance Companies
On October 31, Russian cyber criminal groups KillNet and Beregini announced that they had hacked six of Ukraine’s top insurance companies and gained access to personal data on 7 million Ukrainians.
A representative of KillNet told the Russian state media outlet RIA Novosti that the data would be provided to the Kremlin to persecute Ukrainians involved in the war effort.
“…after Russia’s victory in the special military operation, all information will be used to identify those potentially connected to Ukrainian radicals and to subsequently initiate criminal cases against Nazis, the GUR agent network, the SBU, and those who served in the ranks of the Ukrainian Armed Forces and disseminated pro-Nazi propaganda online.”
Iranian Hackers Target Top Israeli Defense Firm
Iranian cyber proxy group Cyber Isnaad Front announced on October 31 that it had hacked into top Israeli defense contractor, Maya.1 The group claimed that it had obtained classified files on the company’s work for 36 Israeli and Western military projects, including the Iron Beam 450 air defense laser system. It is selling the schematics for the military systems on the dark web for between $1K and $18M
Cyber Isnaad Front also published personal data on company employees, and encouraged its followers to target them.
Takeaways:
On the Chinese Hack
Google Threat Intelligence Group describes UNC6384 as a “PRC-nexus cyber espionage group believed to be associated with the PRC-nexus threat actor TEMP.Hex (also known as Mustang Panda)”
The UNC6384 campaign exploited the ZDI-CAN-25373 Windows vulnerability which was identified in March 2025.
Arctic Wolf notes that the nature of spear-phishing attacks set out for Belgian diplomats suggests an interest in understanding NATO’s defense procurement. Lures for Hungarian diplomats suggest an interest in understanding trade between the EU and Western Balkans.
Cyber security firm StrikeReady believes the targeting of Serbian government officials was likely motivated by an interest in better understanding how the country tries to balance its ties with the European Union with those of Russia and China.
On the Russian Hack
KillNet and Beregini are Russian cyber crime groups which have pivoted to hackivism in support of the Kremlin since the 2022 invasion of Ukraine. While not proven, the nature of the groups’ operations suggest a degree of coordination with the Russian intelligence services.
While a goal of the KillNet and Beregini hacking operation is to demoralize Ukrainian civilians, its bigger strategic purpose is likely to identify potential sources that can be exploited by Russian intelligence. The information provided by the insurance hack can identify individuals who have poor credit and other significant financial difficulties—a prime target for any intelligence service. Russian intelligence officers can entice these vulnerable individuals with offers of money in exchange for information or participation in sabotage operations.
This is the third major hack of Ukrainian companies claimed by KillNet and Beregini in two weeks. On October 21, KillNet announced that it hacked the Ukrainian drone market place Brave1 and obtained proprietary information for numerous advanced Ukrainian drones. Two days later on October 23, KillNet and Beregini announced that they had hacked into the drone manufacturer Warbirds for Ukraine and obtained sensitive employee data.
It is worth noting that KillNet is known to exaggerate its claims and its new announcements should be treated with skepticism. For example, in August 2025, KillNet claimed that it had hacked the Ukrainian General Staff and obtained evidence that 1.7M Ukrainian soldiers were killed or missing in combat since 2022. This number likely exceeds the total number of Ukrainians to have served in the armed forces since 2022.
On the Iranian Hack
Cyber Isnaad Front is an Arab language hacking group that targets Israeli defense companies and doxxes their employees. The group claims to be a volunteer hackivist group affiliated with the broader “axis of resistance.” However, as Ari Ben Am of the Foundation for Defense of Democracies documents, the group appears to be an Iranian Revolutionary Guard Corps (IRGC) front group started during the 12-Day War between Iran and Israel. Extensive promotion of Cyber Isnaad Front’s work on Tasnim News, the mouthpiece of the IRGC, appears to affirm this link.
This latest incident closely resembles the “hack-and-leak” operations that have become a standard cyber espionage practice of the IRGC in recent years.
7. NORTH KOREA DECLARES WILLINGNESS TO DEFEND PEACE IN EURASIA FROM WESTERN THREATS
Speaking at the Third Minsk International Conference on Eurasian Security in Belarus on October 28, North Korean Foreign Minister Choe Son-hui announced that Pyongyang is “prepared to respond to all threats looming over the Eurasian continent,” and is “fully committed to maintaining peace and security on the Korean Peninsula and beyond.”
Takeaways:
FM Choe Son-hui’s statement is not an indication that North Korea intends to deploy more troops to other combat zones, or even continue its deployments to Russia. It is however, a sign that North Korea no longer feels isolated and sees itself as a rising regional power.
North Korea will likely continue to leverage its combat experience in Russia and its role supplying the Russian military to seek new buyers for its weapons.
8. NORTH KOREAN NAVY TESTS NEW MISSILE SYSTEM
On October 29, the North Korean Navy test fired “sea-to-surface strategic cruise missiles” in the Yellow Sea. North Korean state media claims the missiles flew for over two hours before hitting their targets.
Takeaways:
The missile test occurred during naval exercises involving the country’s newest 5,000-ton Choe Hyon-class destroyers. It is not immediately clear whether the destroyers fired the missiles, though the new destroyers have vertical launch systems (VLS) that need to be tested.

VLS cells on the rear of the Choe Hyon on October 5, 2025. Source: KCNA via Naval News This is North Korea’s second missile test in two weeks after months of no missile tests. As noted in the Weekly Significant Activity Report - October 25, 2025, these tests appear timed to coincide with this week’s APEC CEO Summit, signaling Pyongyang’s influence over events on the Korean peninsula and its desire to capture President Trump’s attention.
OPFOR Journal will not be providing a link for Cyber Isnaad Front’s claims to avoid spreading details which may compromise the safety of the company’s employees.






Thank you for a thorough update. Will there be any coverage of the conflicts in Africa? Like in Burkina Faso?