Homeland Security Brief - November 2025
This brief highlights significant threats to US homeland security posed by China, Russia, Iran, and North Korea observed between October and November 2025.
Summary:
Observed Threats - Current activity that poses direct risk to US homeland security
A series of reports issued between October and November have detailed evidence that cyber threat actors from China, Russia, Iran and North Korea are using artificial intelligence (AI) to improve the effectiveness of their malicious cyber operations and deploy novel forms of malware.
The IndieChina Film Festival, set to open November 8 in New York City, was canceled after organizers faced a coordinated harassment campaign from Chinese individuals and groups.
On November 5, the US Department of Justice charged three Chinese scholars conducting research at the University of Michigan with illegally smuggling roundworms into the US. It is the second time this year that Chinese researchers at the university have been arrested for smuggling dangerous biological materials into the country.
Russia is using untracked shadow fleet vessels that are unsuitable for travel in the Arctic to transport petroleum products through the Northern Sea Route. The practice raises the risk of environmental disaster, particularly near the northern coast of Alaska.
Horizon Threats - International activity that may pose future risk to US homeland security
Norway and Israel have identified serious security vulnerabilities in Chinese-made electric vehicles (EVs).
Mexican security forces foiled an Iranian plan to assassinate the Israeli ambassador to the country during the summer. The plot by Unit 11000 of the Iranian Revolutionary Guard Corps is part of a broader campaign by Iran to target and attack Jews and Israeli citizens around the world.
North Korean hackers are using the South Korean messaging service KakaoTalk to deploy malware on Android devices, then remotely resetting the devices to cover their tracks. The campaign has targeted at least one prominent North Korean defector who attended the UN General Assembly in New York in May.
OBSERVED THREATS
Current activity that poses direct risk to US homeland security
1. CHINA, RUSSIA, IRAN, NORTH KOREA USING AI TO FACILITATE CYBER OPERATIONS
Google Announces That it Has Observed Hackers from China, Russia, Iran, North Korea Using AI Powered Malware
On November 5, Google’s Threat Intelligence Group released a new report: “GTIG AI Threat Tracker: Advances in Threat Actor Usage of AI Tools.” The report disclosed evidence that threat actors in China, Russia, Iran, and North Korea are all operationalizing the use of artificial intelligence for use in malware. These uses included emergent marketplaces for AI tools used to construct malware as well as automated programming workflows to scan code bases for vulnerabilities and then to tailor malware to exploit them.
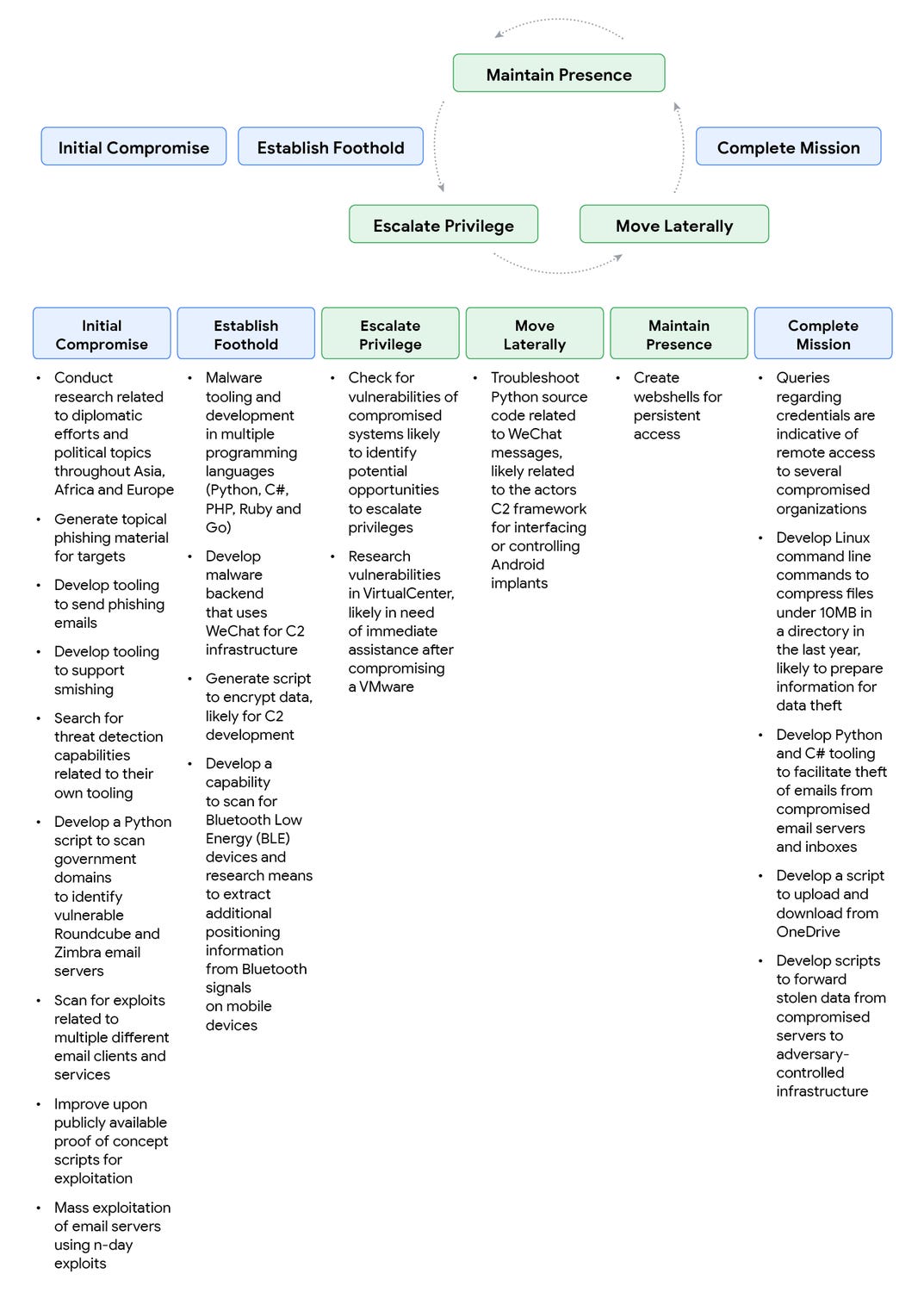
The report also identified a novel AI-enhanced malware by Russian actors against Ukraine over the summer. The AI malware interacted with open-source large language models during its deployment. According to the report:
“In June, GTIG identified the Russian government-backed actor APT28 (aka FROZENLAKE) using new malware against Ukraine we track as PROMPTSTEAL and reported by CERT-UA as LAMEHUG. PROMPTSTEAL is a data miner, which queries an LLM (Qwen2.5-Coder-32B-Instruct) to generate commands for execution via the API for Hugging Face, a platform for open-source machine learning including LLMs. APT28’s use of PROMPTSTEAL constitutes our first observation of malware querying an LLM deployed in live operations.
“PROMPTSTEAL novelly uses LLMs to generate commands for the malware to execute rather than hard coding the commands directly in the malware itself. It masquerades as an ‘image generation’ program that guides the user through a series of prompts to generate images while querying the Hugging Face API to generate commands for execution in the background.”
OpenAI Releases New Report Detailing Misuse of ChatGPT by Russian, North Korean, and Chinese Threat Actors
In October, OpenAI released a report “Disrupting Malicious Uses of AI: An Update.” The report identified cases in which groups in Russia and North Korea used ChatGPT to craft and deploy malware. Russian threat actors used multiple ChatGPT accounts to design and assemble building blocks of a malware sequence to circumvent restrictions, while North Korean threat actors used ChatGPT to improve their programming workflows.
The report also identified threat actors associated with the Chinese government using ChatGPT to support internal surveillance and transnational repression. Several of these threat actors requested information on developing social media listening tools. In several cases Chinese actors requested specific information on social media users critical of the Chinese government.
North Korean Hackers Observed Using AI Filters in Interviews for Remote IT Jobs
Famous Chollima, a North Korean Advanced Persistent Threat Actor affiliated with the Lazarus Group, has been observed by researchers at Mexican FinTech firm Bitso Quetzal using AI filters to alter their appearance for remote work interviews at the firm.
The North Korean hackers applied for software engineering positions at the company using the names and resumes of Mexican and Colombian nationals and attended video interviews using real-time AI face filters to disguise their appearance.
North Korean Hackers Using AI for Crypto Heists
In an October 25 interview with CoinDesk MystenLabs co-founder Kostas Chalkias claims that North Korean hackers are rapidly experimenting with large language models to scan the code base of blockchains and exploit vulnerabilities.
Additional Information:
On the Use of AI in Cyber Operations:
Google previously reported in January 2025 that China, Russia, and North Korea had been using AI to enhance their cyber operations. However, this previously documented use of AI was primarily for research purposes and to increase productivity. The appearance of LLM-querying malware in the new report suggests the three countries are rapidly adapting novel means of using AI for malicious ends.
On North Korean Cyber Operations:
As the sophistication of North Korea’s crypto heists and IT remote work fraud schemes grows, so does their pay out. According to a new series of US sanctions announced on November 4, North Korea is believed to have laundered over $3B through cyber crime over the past three years. The money laundered flows through North Korean individuals and financial institutions stationed in Russia and China.
According to an October 22, 2025 report by the Multilateral Sanctions Monitoring Team (MSMT) the money obtained through these schemes has been a major source of revenue to fund the North Korean ballistic missiles and nuclear weapons programs.1 The MSMT has identified a nine-step pattern that North Korea uses to turn its illicit funds into money it can use.

2. CHINESE PRESSURE CANCELS NEW YORK FILM FESTIVAL
On November 6, the inaugural IndieChina film festival—“dedicated to showcasing the diverse, bold, and thought-provoking world of Chinese independent cinema”—was canceled due to harassment and intimidation from individuals and organizations in China. The festival had been scheduled to run November 8-15 in New York City.

According to Human Rights Watch, the harassment targeted several dozen film directors and producers as well as their families in China, and even extended to non-Chinese filmmakers.
Additional Information:
While IndieChina was not an overtly political event, its targeting reflects the Chinese Communist Party’s broader ideological goal under Xi Jinping to control global perceptions of China. Since 2012, the Xi government has curbed independent filmmakers in China and Hong Kong and increasingly targeted film and other media productions abroad that portray the country unfavorably.
In July, Beijing tried to block the international release of the Filipino documentary “Food Delivery: Fresh from the West Philippine Sea,” which chronicles the impact of aggressive Chinese maritime expansion on Philippine fisheries by pressuring film festival organizers in New Zealand. In August, Chinese officials similarly tried to pressure the Bangkok Arts and Cultural Centre in Thailand into closing an exhibit by Tibetan, Uyghur and Hong Kong artists critical of Beijing.
The targeting of IndieChina is also illustrative of Beijing’s strategy of disciplining overseas Chinese communities into promoting only official narratives of the Chinese Communist Party as part of its “United Front Work.” The US House Select Committee on Strategic Competition Between the United States and the Chinese Communist Party, has identified multiple instances of similar united front work in the US. These include 2023 protests against Taiwanese President Tsai Ing-wen’s US visit, in which Chinese consulate officials in Los Angeles allegedly paid protesters, and the operation of an illegal “police station” in New York in 2022 used to surveil overseas Chinese residents.
On November 7, one day after the IndieChina film festival was canceled, the Chinese People’s Political Consultative Conference (CPPCC) discussed the country’s strategy for “encouraging overseas Chinese to introduce China in a comprehensive and objective way, so as to enhance the international community’s understanding of the country.”
Screenshot of the CPPCC press release discussing Beijing’s influence over Chinese populations overseas. Source: CPPCC
3. CHINESE SCHOLARS CHARGED WITH SMUGGLING DANGEROUS BIOLOGICAL MATERIALS INTO THE US
On November 5, the US Department of Justice announced the arrest and charging of three Chinese nationals attending the University of Michigan on J-1 visas with conspiracy to smuggle biological materials into the United States and making false statements to federal agents. The scholars had received multiple shipments of “concealed biological materials related to roundworms” from a researcher in China between 2024 and 2025.
Additional Information:
While it is not clear if this case involved malicious intent, the incident is suspicious nonetheless as it is not the first time Chinese scholars and researchers at the University of Michigan have smuggled dangerous biological materials into the US this year.
In June 2025, two Chinese scholars at the University of Michigan, including one member of the Chinese Communist Party, were arrested and charged with smuggling Fusarium graminearum into the US. Fusarium graminearum is a toxic fungus that destroys cereal crops and can cause illness and death in humans and livestock.
4. RUSSIA’S SHADOW FLEET RISKS ENVIRONMENTAL DISASTER IN THE ARCTIC NEAR ALASKA
On November 12, The Barents Observer reported that Russia’s Northern Sea Route Administration has stopped providing reliable data on Russian shipping along the Northern Sea Route. Data is likely being withheld to disguise the increasing number of sanctions-evading vessels of Russia’s “shadow fleet” using the route.
The Barents Observer noted that the loss of accurate Russian shipping data is particularly problematic because Russia is simultaneously authorizing more non-ice class vessels to operate in the Arctic. Both factors greatly increase the likelihood of an environmental disaster as tankers carrying oil and liquefied natural gas (LNG) make up the majority of Russian shipping along the route.
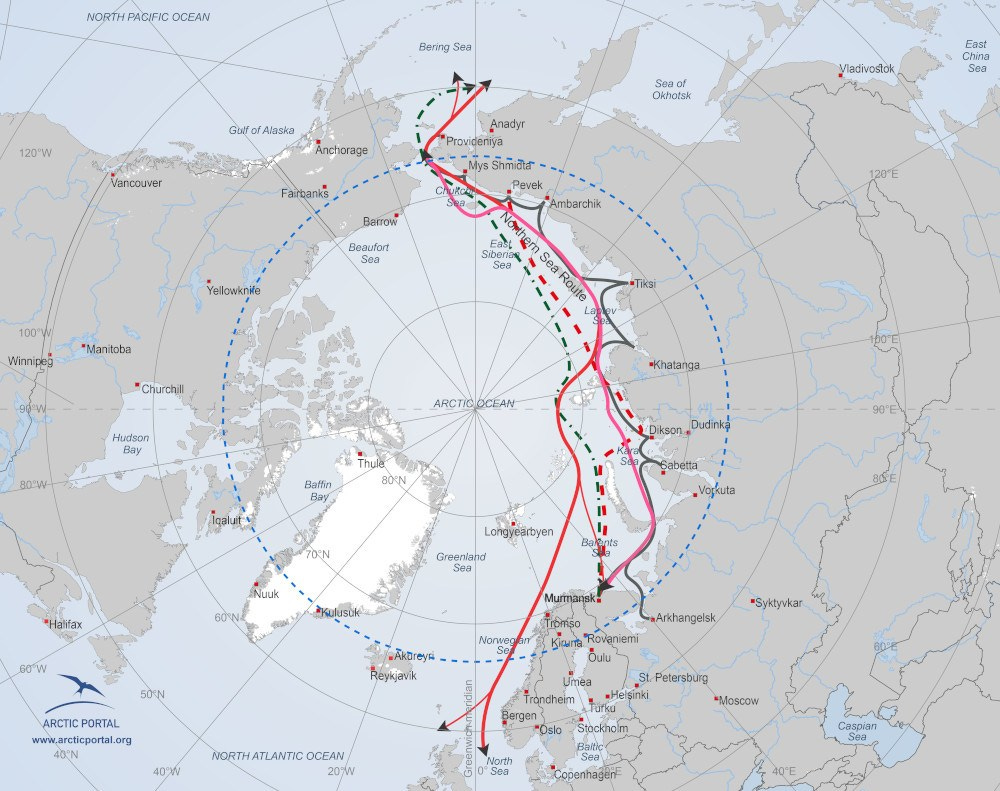
Additional Information:
The risk of environmental disaster is particularly acute near Alaska. The Chukchi Sea near Alaska is considered to be one of the most hazardous portions of the Northern Sea Route. Tankers make up the largest portion of Russian traffic through the region.
In September, a non-ice-class Russian shadow fleet vessel carrying LNG, the Arctic Metagaz, nearly became stuck in ice in the East Siberian Sea. Data related to Arctic Metagaz has been scrubbed from the Northern Sea Route Administration’s tracker.
HORIZON THREATS
International activity that may pose future risk to US homeland security
5. SERIOUS SECURITY VULNERABILITIES FOUND IN CHINESE ELECTRIC VEHICLES SOLD ABROAD
Chinese Electric Buses Come Under Scrutiny in Scandinavia
Norwegian public transportation operator Ruter has discovered that the Chinese electric buses in its fleet can be remotely controlled by their manufacturer Yutong Group. Ruter claims that while cameras on the bus are not connected to the internet, the bus’ batteries and power systems can be remotely accessed and disabled.
The findings have led the governments of the UK, Norway, and Denmark to launch investigations into security vulnerabilities posed by Chinese electric vehicles.
Israeli Military Dumping Chinese Electric Vehicles Due to Security and Surveillance Concerns
On November 2, Israel Hayom reported that the Israeli General Staff had ordered the collection and removal of 700 Chinese-made electric vehicles used by the Israeli Defense Forces. The Israeli General Staff deemed the vehicles a security risk due to their ability to passively collect audio, video, geospatial data, and potentially other forms of intelligence and transmit data back to manufacturers in China.
The vehicles, which are mostly from Chery, will be exchanged for Japanese models.
Additional Information:
Restrictions and tariffs imposed on Chinese electric vehicles have reduced security risks associated with Chinese electric vehicles in the US.
However, increasing numbers of Chinese EVs could enter the US either on a temporary basis or through secondary markets through Canada in the future if Ottawa drops its own tariffs on the vehicles. While this would pose little risk to US markets, it would require evaluating access restrictions for Chinese-made EVs near critical infrastructure and other sensitive facilities, given their potential use as remote surveillance and listening devices.
Third-party research has confirmed that Chinese EVs routinely transmit data to and from manufacturers in China. With thousands of embedded chips, these vehicles represent far more sophisticated surveillance and listening devices than other Chinese electronics. A key concern is the potential for Chinese-made vehicles to passively collect intelligence on individuals near sensitive facilities for further exploitation by human intelligence operatives, or to connect with facility IT systems to remotely extract electronic data or deploy malware.
The most significant security risk from this scenario may not involve government installations, but rather US tech company sites, such as corporate headquarters and data centers, where many Canadian tech workers are employed and may drive Chinese EVs in the future.
Officials in Australia and the UK have increasingly voiced similar concerns about security threats posed by Chinese EVs. The shared concerns present an opportunity for all Five Eyes countries (the joint intelligence enterprise of Australia, Canada, New Zealand, UK, and the US) to work together to adopt shared security standards related to these vehicles.
6. IRAN PLOTTED TO ASSASSINATE ISRAEL’S AMBASSADOR TO MEXICO
On November 7, US officials announced that Unit 11000 of the Iranian Revolutionary Guard Corps’ (IRGC) elite Quds Force plotted to assassinate Israel’s Ambassador to Mexico earlier this year. The months-long plot was stopped by Mexican security forces during the summer.
Additional Information:
The operation was allegedly planned out of the Iranian Embassy in Venezuela. The Quds Force has maintained a presence in Venezuela since the presidency of Hugo Chavez in the early 2000s. The group uses Venezuela and connections with the country’s leaders to conduct drug trafficking and money laundering to finance IRGC operations.
Iran has plotted similar assassinations in the US, including targeting President Donald Trump and members of the first Trump Administration, and high-profile political dissidents such as Masih Alinejad.
An October 26, 2025 statement by Israel’s Mossad national intelligence agency asserted Unit 11000’s involvement in coordinating numerous plots to attack Jews and Israelis in Europe and Australia over the past year. Mossad alleges that Unit 11000 recruits local criminals and disaffected foreigners in host countries and coordinates their participation in violence against Jews.
The statement follows an August announcement by the Australian government attributing two arson attacks on a synagogue in Melbourne and a Jewish-owned restaurant in Sydney to operatives of the IRGC. Both incidents involved IRGC members coordinating local actors through a web of intermediaries. The incidents, as well as other suspected plots, subsequently moved Australia to label the IRGC a terrorist organization, and expel the Iranian ambassador from the country.
7. NORTH KOREAN HACKERS REMOTELY TARGETING AND WIPING PHONES
South Korean cyber security company Genians has documented new North Korean hacking tactics which use South Korean messaging app KakaoTalk to distribute malware and Google’s “Find Hub” to remotely infiltrate and wipe Android devices.
North Korean APT groups KONNI, Kimsuky, and APT 37 initiate these attacks using spear phishing lures to infiltrate victims’ systems. After gaining access, these threat actors conduct long-term surveillance of a user’s activities—including webcam monitoring—before deploying malware through their KakaoTalk account. To conceal their activities, the threat actors exploit Google’s “Find Hub” feature to remotely locate, access, and factory reset the victim’s Android devices.
South Korean police allege that APT group Kimsuky used this tactic to target outspoken North Korean defector Kim Eun-ju’s phone. That attack led Kim Eun-ju’s KakaoTalk to spread malware concealed as a mindfulness and stress relief app.
Additional Information:
Kim Eun-ju attended the UN General Assembly in New York City in May where she participated in a meeting on the human rights situation in North Korea and North Korea’s dispatch of troops to Russia. Kim Eun-ju was likely targeted as a means of mapping a broader network of North Korean defectors and their supporters. It is not clear at this time if Kim’s devices were infected while she was in New York.
The MSMT is composed of officials from the governments of the US, Australia, Canada, France, Germany, Italy, Japan, the Netherlands, New Zealand, the Republic of Korea, and the UK.




This piece really made me think about the AI angle; the detail about threat actors leveraging it for cyber ops is incredibly insightful and something I track closely. It's a sobering report that really empasizes the constant need for proactive digital defense on a global scale.