Homeland Security Brief - December 2025
This brief highlights significant threats to US homeland security posed by China, Russia, Iran, and North Korea observed between November and December 2025.
Summary:
Observed Threats - Current activity that poses direct risk to US homeland security
Russian Navy Auxiliary General Intelligence Ship Kareliya loitered in international waters off the coast of Oahu, Hawaii for two weeks likely conducting surveillance on US military installations and signals intelligence collection.
Senior Russian astronaut Oleg Artemyev was removed from an upcoming joint US-Russian SpaceX Crew-12 mission to the International Space Station (ISS) after an apparent attempt at industrial espionage.
New cyber threat intelligence assessments suggest Russia is replacing costly zero-day exploits with lower-cost, higher-volume attacks on US critical infrastructure involving hacktivist groups and cybercriminals and exploits of vulnerabilities in networking devices.
Leading US AI company Anthropic reports observing Chinese state-sponsored threat actors use its AI programming application Claude Code to perform the first ever, nearly fully autonomous cyber attacks.
A new report by the Associated Press has found that Chinese security services are tracking and intimidating perceived enemies in America using US big data analytics programs.
The FBI warns in its 2025 “Worldwide Threats to the Homeland” briefing that Iran remains focused on assassinating US officials involved in the January 2020 killing of Qasem Soleimani, and continues to surveil Jewish and Israeli targets in the US.
Horizon Threats - International activity that may pose future risk to US homeland security
Anti-American disinformation sourced from Russian state media has proliferated in Mexico in 2025.
Pro-Beijing activists are targeting female Chinese dissidents as well as female relatives of male dissidents with deepfake pornography in Australia, Canada, and the UK.
OBSERVED THREATS
Current activity that poses direct risk to US homeland security
1. RUSSIAN INTELLIGENCE SHIP SURVEILS HAWAII
On November 13, the US Coast Guard announced the presence of the Russian Navy Auxiliary General Intelligence Ship Kareliya operating 15 nautical miles off the coast of Oahu. The vessel had arrived in late October and remained in the area for over two weeks before the announcement.

Additional Information:
The Kareliya likely conducted surveillance on Oahu’s extensive military bases and signals intelligence centers.
The Kareliya’s operations near Hawaii coincided with that of another Russian intelligence ship off the coast of the UK. On November 19, British Defence Secretary John Healey announced the presence of the Yantar, a Russian Project 22010 class oceanic research vessel off the coast of the British Isles. The ship responded aggressively to efforts by the Royal Air Force to monitor it, targeting passing aircraft with high-powered optical lasers.
The simultaneous operation of both intelligence vessels may have been an effort by the Kremlin to push back against pressure to end the war in Ukraine.
2. RUSSIAN ASTRONAUT EXPELLED FROM SPACEX FLIGHT
In late November, experienced Russian astronaut, Oleg Artemyev, was removed from the upcoming SpaceX Crew-12 mission to the International Space Station (ISS) due to alleged violations of the International Traffic in Arms Regulations (ITAR). Artemyev allegedly photographed SpaceX engine components and other sensitive technology and documents during training at SpaceX’s headquarters in California and then exported them to unknown persons through his phone.
Additional Information:
The circumstances of the case, while still largely unknown, nevertheless suggest Artemyev was engaging in deliberate industrial espionage. Russian space industry expert Georgy Trishkin explained to Russian investigative journalist outlet The Insider, “It’s very difficult to imagine a situation in which an experienced cosmonaut could inadvertently commit such a gross violation.”
It is less clear whether the Russian government directed or incentivized Artemyev’s snooping. While Russia has strong incentives to avoid disrupting space cooperation with the US, the Russian government may be willing now to take risks to avoid falling behind the rapidly developing American and Chinese space programs. The US Space Force’s September 2025 Space Threat Fact Sheet assesses that while the Russian space industry remains a world leader, its overall launch capacity has been declining in recent years, and has been surpassed by both the US and China:
“Russian space technology has declined amid funding shortfalls, international isolation, and broader societal problems. Russia conducted only 17 launches in 2024—well short of the 26+ annual launches it averaged from 1995 to 2015—and remained largely absent from the international market, launching only five foreign payloads. Russia retains expertise in rocket engines and space launch; however, its launch activity increasingly lags the U.S. and China. Russia aspires for its newest cosmodrome to reduce dependencies on Baikonur. Russia operates advanced ISR satellites for optical imagery, SIGINT, and missile warning, but Moscow is increasingly relying on civil and commercial providers. For example, Russian private military companies have purchased imagery from Chinese company Spacety to support combat operations in Ukraine.”
The precarious state of Russia’s space program was exemplified on November 27, 2025 when the Soyuz MS-28 mission launching US and Russian astronauts to the ISS severely damaged the Gagarin 31 launch pad at the Baikonur Cosmodrome—the only launch pad available to Russia capable of supporting manned missions. The incident has left Russia without the ability to launch manned space flights for the first time since 1961. Roscosmos claims the launch pad will be repaired by February 2026, however some industry observers believe the repairs could take many more months or even years to complete.
3. RUSSIAN HACKERS CHANGING TACTICS TO TARGET US CRITICAL INFRASTRUCTURE
Charges Announced Against Pro-Russian Hackivists
On December 9, the Cybersecurity and Infrastructure Security Agency (CISA) released a joint advisory warning of ongoing opportunistic attacks on US critical infrastructure by pro-Russia hacktivist groups. The groups named included CARR (CyberArmyofRussia_Reborn), Z-Pentest, NoName057(16), and Sector16.
On the same day the FBI announced charges against CARR member Victoria Eduardovna Dubranova for her role in conducting cyberattacks on critical infrastructure worldwide on behalf of the interests of the Russian government.
Russian Military Intelligence Targeting Amazon Web Services
On December 15, Amazon Threat Intelligence announced it had observed a years-long campaign by threat actors linked with Russian Military Intelligence (GRU) targeting Western critical infrastructure, energy companies, and web service providers. The actors exploited misconfigured customer network edge devices such as routers, VPN configurations, and network management applications, as well as project management and cloud-based collaboration platforms, to gain control of operational systems.
Additional Information:
An August 2025 FBI Internet Crime Complaint Center bulletin noted that Russia’s Federal Security Service (FSB) has similarly focused on exploiting networking device vulnerabilities, indicating a shift in Russian state-sponsored hacking from expensive zero-day and N-day exploits to lower-cost attack methods.
This shift to lower-cost cyber attacks is evident in Kremlin support for hacktivist and cybercriminal groups. Nationalist cybercriminal groups such as KillNet and Beregini have emerged as leading Russian cyber proxies in Ukraine, intimidating civilians, stealing government records, and conducting industrial espionage against Ukrainian drone manufacturers.
4. ANTHROPIC REPORTS CHINESE AI AUTOMATED CYBER ESPIONAGE CAMPAIGN
On November 13, leading US AI company Anthropic reported that it had observed Chinese state-linked hackers use its AI coding application, Claude Code, to conduct nearly fully automated cyber espionage campaigns through autonomous attack frameworks in mid-September 2025.
According to Anthropic, the Chinese threat actors used Claude Code to develop autonomous attack frameworks that would allow multiple AI agents to cooperate together to conduct complex operations in sequence.
“The threat actor developed an autonomous attack framework that used Claude Code and open standard Model Context Protocol (MCP) tools to conduct cyber operations without direct human involvement in tactical execution. The framework used Claude as an orchestration system that decomposed complex multi-stage attacks into discrete technical tasks for Claude sub-agents—such as vulnerability scanning, credential validation, data extraction, and lateral movement—each of which appeared legitimate when evaluated in isolation. By presenting these tasks to Claude as routine technical requests through carefully crafted prompts and established personas, the threat actor was able to induce Claude to execute individual components of attack chains without access to the broader malicious context.”
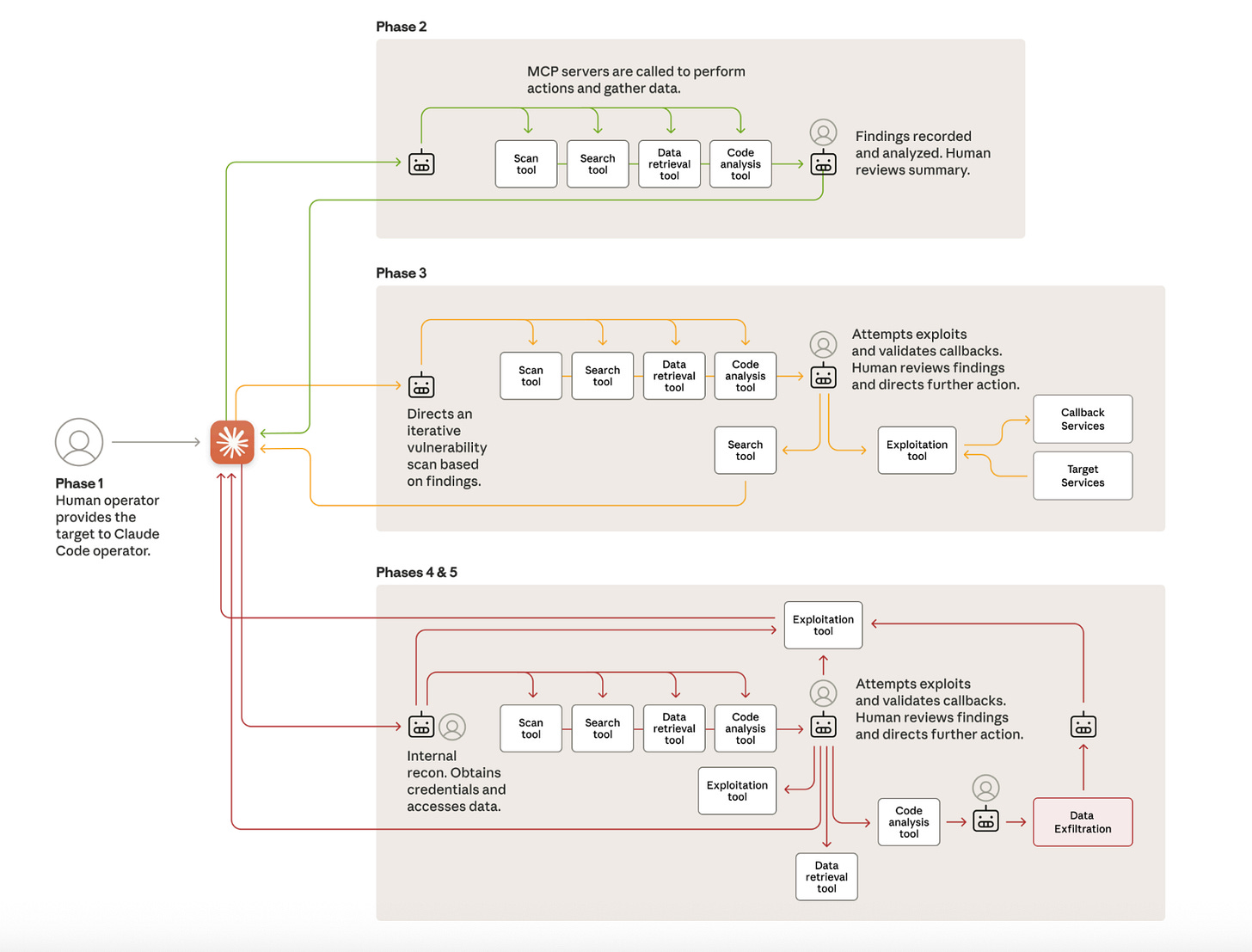
The cyber operations targeted several “large tech companies, financial institutions, chemical manufacturing companies, and government agencies,” and in several cases appeared to successfully infiltrate their targets.
Additional Information:
A study by researchers at Stanford University, Carnegie Mellon University and Gray Scale AI published on December 12, 2025 previewed the potential threat posed by AI agentic hackers using autonomous attack frameworks. The researchers created an agentic framework called ARTEMIS that allowed multiple AI agents to cooperate to conduct penetration testing on Stanford University’s computer networks. The group of AI agents working together as ARTEMIS outperformed 9 of 10 human researchers given the same tasks, while costing a fraction of the price at approximately $18 per hour.
The researchers noted that while ARTEMIS and human participants followed similar procedures and workflows, their skill sets differed. ARTEMIS excelled at multi-tasking, assigning sub-agents to probe already discovered vulnerabilities while continuing to scan for other targets. Human participants, on the other hand, tended to more effectively focus on fully exploiting individual vulnerabilities and were better able to assess the completion of tasks.
5. CHINA USING US TECH AND COOPERATION WITH INTERNATIONAL LAW ENFORCEMENT TO HUNT PERCEIVED ENEMIES IN THE US
A December 12 report by the Associated Press used the case of former Chinese official Li Chuanliang to expose how China leverages US-made surveillance technology in its “Sky Net” and “Fox Hunt” operations to hunt down perceived enemies abroad. Since Li fled to the US and became a whistleblower, Chinese authorities have investigated and detained over 40 of his friends, family members, and associates (three of his former colleagues who were detained are believed to have died in custody) while operatives have traveled to New York, California and Texas to stalk him.
The report revealed China’s systematic use of American technology, particularly from IBM, Oracle and Microsoft to conduct big data analysis to track wanted individuals in the US.
Additional Information:
In March 2025, Chinese state media outlet China Daily reported that since 2015, Operation Sky Net has used global digital surveillance to track down thousands of perceived criminals and internal enemies abroad.
“China has repatriated more than 14,000 fugitives from over 120 countries and regions in the past decade as part of a sweeping anti-corruption campaign, the country’s top graft watchdogs said on Thursday.
“Among them, 2,999 were members of the Communist Party of China and government officials, and authorities had recovered 66.62 billion yuan ($9.3 billion) in illicit assets by the end of last year, according to the Central Commission for Discipline Inspection and the National Commission of Supervision.”
The China Daily report further noted that China had secured the extradition of the majority of its most wanted fugitives through Interpol global arrest warrants, raising concerns about the potential misuse of international law enforcement mechanisms.
“Additionally, 62 of the 100 most-wanted fugitives subject to Interpol Red Notices have been returned to China, the commissions said.”
While China claims Operations Fox Hunt and Sky Net target white-collar criminals, the individuals pursued and the coercive methods employed reveal political motives. Chinese officials routinely threaten and detain family members of wanted individuals as leverage—even when those relatives are US citizens. In 2016, the Chinese government denied an exit visa to a pregnant US citizen for eight months to coerce her mother into returning for trial. The 2020 trial of eight individuals involved in “Fox Hunt” operations in the US exposed a multi-year campaign to stalk a former official’s daughter to pressure him into returning for prosecution.
“Between May 2017 and July 2018, Rong Jing and several co-conspirators allegedly targeted John Doe-1’s adult daughter for surveillance and online harassment. Specifically, Rong Jing attempted to hire a private investigator to locate John Doe-1’s adult daughter in order to photograph and video record the daughter as part of a campaign to exert pressure on John Doe-1. Around the same time, an unidentified co-conspirator sent harassing messages over social media to John Doe-1’s daughter and her friends related to the PRC’s interest in repatriating John Doe-1.”
There are reasonable concerns these pressure campaigns could turn violent or deadly, even absent explicit orders from Beijing. In a December interview with Canadian Broadcasting Corporation, a former Chinese intelligence officer from the Ministry of Public Security’s 1st Bureau, now living in exile in Australia, indicated that the 2022 death of Canadian-based dissident artist Hua Yong—whom the officer had previously targeted—may have been carried out by other operatives within the organization.
6. IRAN CONTINUES TO PLOT ASSASSINATIONS IN US
At the Annual “World-wide Threats to the Homeland” briefing before the House Homeland Security Committee on December 11, Director of the National Counter-Terrorism Center Joe Kent, and FBI Operations Director Michael Glasheen provided an assessment that Iran remains committed to targeting current and former US officials involved in the 2020 assassination of Islamic Revolutionary Guard Corps commander Qasem Soleimani. Glasheen further stated that the FBI believes Iranian-linked actors continue to surveil Jewish communities and Israeli interests in the US, which it may one day target with violent attacks.
Additional Information:
Iran’s assassination operations appear to follow a set playbook. Iran’s Islamic Revolutionary Guard Corps’ (IRGC) elite Quds Force is responsible for coordinating global direct action operations. The Quds Force effectively organizes these operations through subcontractors, to ensure IRGC members have limited direct contact with the individuals conducting surveillance or attacks.
These subcontractors are frequently members of organized crime. The IRGC subcontracted the 2022 attempted assassination of a high-profile Iranian-American dissident Masih Alinejad through the Russian Mob of New York. It subcontracted the 2024 attempted assassination of a pair of Iranian exiles living in Maryland through the Hells Angels motorcycle gang. It similarly organized the 2024 arson of Jewish institutions in Australia through a former chapter leader of the Nomad’s motorcycle gang.
The IRGC generates significant revenue through drug trafficking and maintains extensive contacts with drug cartels across Europe, Asia, and Latin America. It leverages these networks to contract for covert operations including assassinations. In 2011, the IRGC recruited a Los Zetas cartel member in an attempted assassination of the Saudi Arabian Ambassador to the US.
HORIZON THREATS
International activity that may pose future risk to US homeland security
7. RUSSIAN STATE MEDIA SURGING DISINFORMATION IN MEXICO
A November 23, 2025 report by the German Marshall Fund has documented a dramatic increase in citations of Russian state media and other pro-Kremlin media by Mexico’s prominent association of journalists, Club de Periodistas de México, in 2025. The report has found that 54% of all articles posted by the Club’s official publications since April 2025 have included sources from Russia Today, Sputnik, or Cuban government media. Over the same period the Club’s publishing volume also suddenly increased by nearly four-fold from 35.6 articles per week, to 136.9 articles per week. The majority of the new articles published contained talking points from Russian and Cuban sources. These trends suggest the organization has increasingly become a front for laundering Russian and Cuban narratives into Mexican news media.
The New York Times followed this reporting on November 24, with analysis of an April 2024 State Department cable entitled “Mexico: RT’s Invasion” warning that Russian sponsored anti-American propaganda was surging in the country as part of an effort to generate hostilities between the US and Mexico.
Additional Information:
Latin America provides fertile ground for pro-Kremlin disinformation due to deep-rooted anti-American sentiment stemming from decades of U.S. interventionism and lingering nostalgia for Soviet-era support during the Cold War. The Reuters Institute at Oxford University has noted that as of 2023, RT en Español is the most successful of Russia’s foreign media outlets.
8. CHINA TARGETING FEMALE DISSIDENTS WITH DEEPFAKE REVENGE PORN
December reports by Australian, British and Canadian news organizations documented a growing number of cases in which pro-Beijing activists have used AI-generated deepfake pornographic images to target female political dissidents from China and Hong Kong, as well as female family members of male dissidents, living in those countries.
Prominent Chinese-Canadian YouTuber Yao Zhang reported that deepfake pornographic images of her were spread by Chinese agents using hijacked social media accounts of Canadian officials, including former Prime Minister Justin Trudeau. Carmen Lau, a former district councilor and pro-democracy activist in the UK, reported that pornographic deepfakes depicting her were mailed throughout her community with listings advertising sexual services. Ted Hui, a former Hong Kong lawmaker and pro-democracy activist in Australia, reported that explicit deepfake images of his wife were sent to his employer.
Additional Information:
These recent cases represent a more aggressive iteration of a long-running strategy by pro-Beijing activists to combat female activism and pressure male activists through online harassment of their female family members.
This briefing was compiled by Dan White. For more information, corrections, or comments, please contact dan@opforjournal.com




The section on Iran's proxy assassination architecture is particularly wel l-documented. The pattern of subcontracting through organized crime rather than direct IRGC involvement is classic compartmentalization, creating plausible deniability layers while maintaining operational control. What's concerning is how this parallels their regional proxy strategy with Hezbollah and Houthis, basically the same organizational model applied to transnational hits. The examples of using biker gangs and cartels show they're pragmatically leveraging existing criminal infrastructure rather than building from scratch. That makes detection way harder because you're looking for criminal activity that blends into normal organized crime patterns until it's too late.